Much like most operating programs/projects/entities within the Department of Defense (DoD) enforce the Federal Information Security Management Act (FISMA) and Risk Management Framework (RMF – NIST Special Publication 800-53), the new Cybersecurity Maturity Model Certification (CMMC) is the DoD’s attempt at commonly securing and documenting the cyber controls of it’s Defense Industrial Base (DIB).
Following repeated cyberattacks on the DIB, the DoD decided to enforce standards and checks on its contractors and its periphery, much like any program operating on a US Government system. Particularly DIB’s with the following information stored or accessible across that entity’s systems. Beyond that, it is also about maintaining good cyber posture and enforcing some of the same controls done at the DoD program level out to the DIB.
Federal Contract Information (FCI): FCI is information provided by or generated by the Government under contract and not intended for public release.
Controlled Unclassified Information (CUI): CUI is not classified but does require dissemination controls and safeguards per laws, regulations, and policies.
To boil down the need, deciding your need to respond to a particular solicitation seems to be the key to determining which level and when to implement is best for your entity — presently, details are limited.
Timelines
The DoD will be implementing CMMC through a phased rollout approach, which means that not all solicitations will require it until 30SEP25 (as of this article’s writing). The DoD has stated that the targets for solicitations requiring CMMC will be as follows.
- FY21 – 15
- FY22 – 75
- FY23 – 250
- FY24 – 325
- FY25 – 475
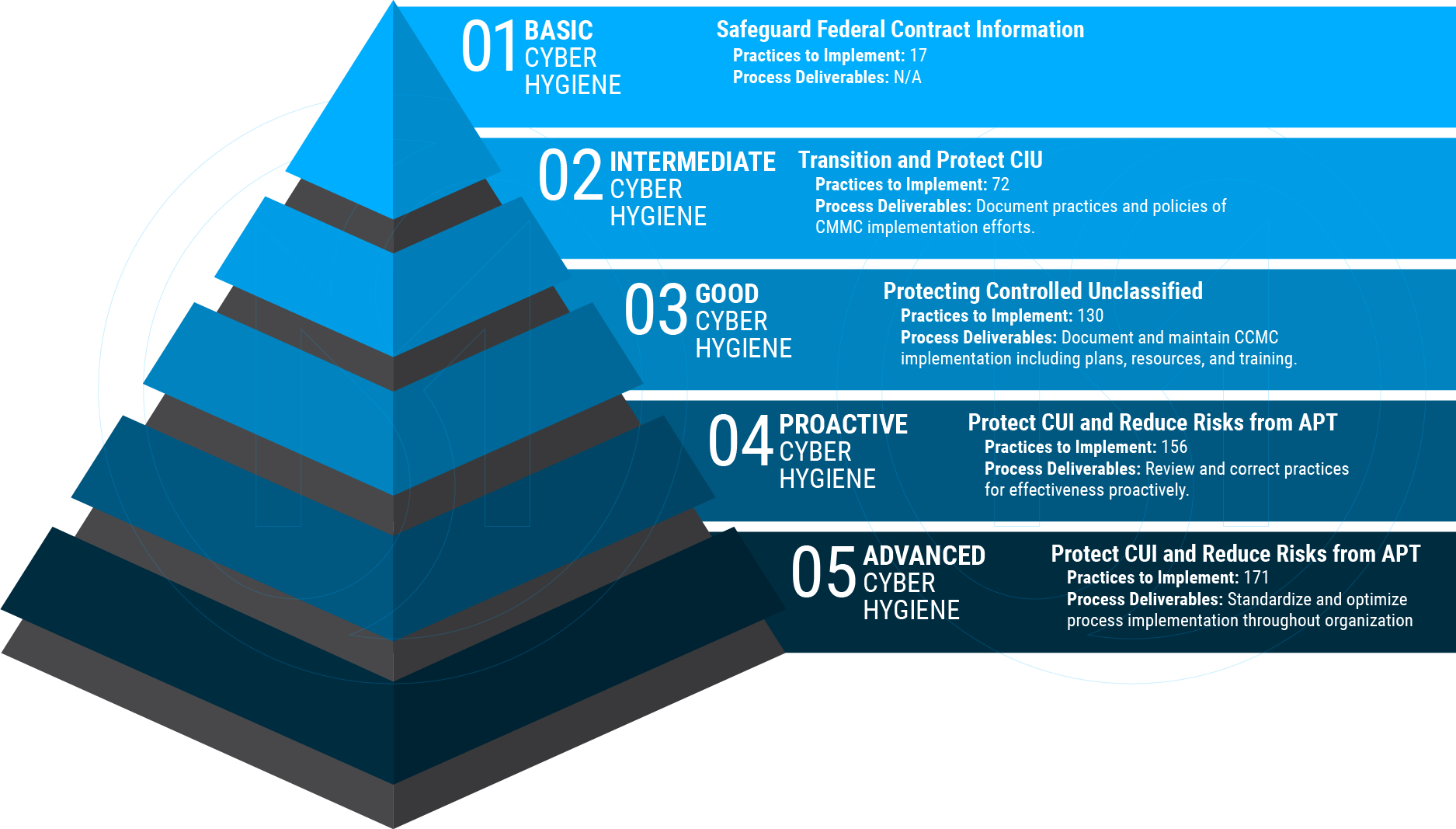
Levels
One of the primary goals was for CMMC to scale to an entity of any size within the DIB. Following a maturity model approach is a great way to accomplish this. It allows for entities to start small and work their way up as needed by contractual requirements. It also does not put an unnecessary burden on smaller entities who can’t afford (or practically require) controls at or above a certain level.
Accreditation / Certification Process
An organization or entity must select which level is right for them and begin implementing and documenting the required controls for each of 12 cyber domains to get started with any certification level. Once correctly implemented, obtain or generate supporting documentation such as practice findings and develop process deliverables following the assessment guides listed here. As the CMMC pulled most of its practices/controls from a couple of guideline documents, most of the content should look familiar to most cyber professionals.
https://www.acq.osd.mil/cmmc/draft.html
- The domains can be found here in section 2.5 of the model
- The current practice to level mappings are located in section 2.7.2
- More details for Level 1 and 3 can be found in their Assessment Guides section
While there are only guides for 1 and 3 at the time of this writing, one can use the practices listed in the CMMC model and use the assessment guides’ standards to derive their documentation.
Selecting an Assessor
Once you’ve gathered, documented, and implemented your practices and processes, head over the CMMC Assessor Board website and search the marketplace for a CMMC-AB for an available C3PAO.
https://portal.cmmcab.org/marketplace/
If you have any questions or comments on this post, leave a comment below. We’re here to help you on your CMMC journey. Contact Us