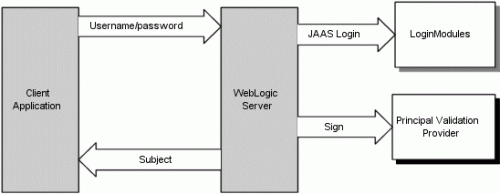
As part of our Oracle Identity Management services, we are consistently configuring environments running WebLogic and integrating deeply with the WLS Security architecture. The following information from the Oracle documentation is a good description of how this is accomplished. It is referred to by Oracle as Perimeter Authentication.
WebLogic Server is designed to extend the single sign-on concept all the way to the perimeter through support for identity assertion. Provided as a critical piece of the WebLogic Security Framework, the concept of identity assertion allows WebLogic Server to use the authentication mechanism provided by perimeter authentication schemes such as the Security Assertion Markup Language (SAML), the Simple and Protected GSS-API Negotiation Mechanism (SPNEGO), or enhancements to protocols such as Common Secure Interoperability (CSI) v2 to achieve this functionality.
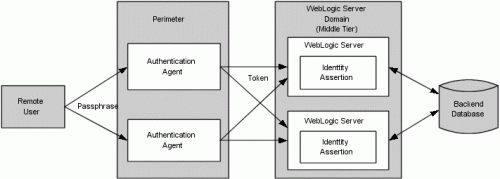
This graphic illustrates perimeter authentication. Support for perimeter authentication requires the use of an Identity Assertion provider that is designed to support one or more token formats. Multiple and different Identity Assertion providers can be registered for use. The tokens are transmitted as part of any normal business request, using the mechanism provided by each of the various protocols supported by WebLogic Server. Once a request is received with WebLogic Server, the entity that handles the processing of the protocol message recognizes the existence of the token in the message. This information is used in a call to the WebLogic Security Framework that results in the appropriate Identity Assertion provider being called to handle the verification of the token. It is the responsibility of the Identity Assertion provider implementation to perform whatever actions are necessary to establish validity and trust in the token and to provide the identity of the user with a reasonable degree of assurance, without the need for the user to re-authenticate to the application.
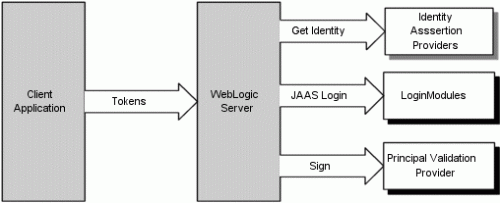
Following is a diagram of the perimeter authentication process we follow when configuring customers with SSO, including Windows Native Authentication. You will notice the addition of the Identity Asserter, which sends back a username to WebLogic: